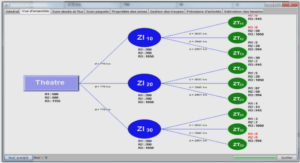
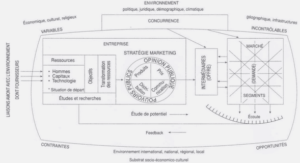
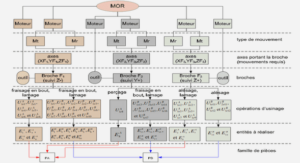
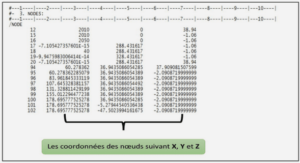
Extrait du course Unix installing and running the Tripwire product
Purpose and scope
This user’s guide is for the UNIX administrator responsible for installing and running the Tripwire product. It is specifically designed for less-experienced users who are familiar with UNIX systems.
Conventions
The following conventions apply:
Boldtype helps identify security issues.
<Italic> or Italic type identifies user-defined or context-specific material:tripwire -m p –site-keyfile ../key/key-file.key myfile.txt Italic type identifies vocabulary specific to Tripwire software or its field, integrity assessment.
Brackets [ ] encase an optional argument.
{Braces} encase multiple options, of which one must be chosen. The token | delimits each option: {1 | 2 }.
./ is specified as the path for all Tripwire commands. This convention is recommended to ensure that Tripwire commands execute from the current directory, and to protect against Trojan Horse attacks.
Related documents
In addition to this guide are man pages, a policyguide.txtfile, and a Quick Reference Card.
Latset information and support
You can get the latest information through discussion groups at:
http://www.tripwiresecurity.com/support/dgroups.html
The Tripwire Security Systems technical support staff can be reached at:
http://www.tripwiresecurity.com/supintro.html
If necessary, you can send email to “support@tripwiresecurity.com” or call 1-877-TRIPWIRe.
Introduction to tripwire software
1.0 Overview
This section is intended for system administrators who are new to Tripwire software or who are unfamiliar with the concepts of integrity assessment. Experienced Tripwire users may want to skip to Section 1.5, New Features in this Release, or to Chapter 2, Installing Tripwire Software. This section describes:
• What Tripwire software is
• Deploying Tripwire software
• How Tripwire software works
• Changes for Tripwire 2.2.1
1.1 What Tripwire Software Is
Tripwire 2.2.1 is a tool for file integrity assessment, a form of intrusion detection that works in conjunction with firewalls and other technologies to provide the most fundamental layer of defense within the enterprise.Tripwire software works by first scanning a computer and creating a database of system files, a compact digital “snapshot” of the system in a known secure state. You can configure Tripwire software very precisely,
specifying individual files and directories on each machine to monitor, or you can create a standard template for use on all machines in an enterprise.
1.2 Deploying Tripwire Software
Tripwire 2.2.1 is not meant to replace your firewall or other perimeter security measures. Instead, Tripwire software is host-based, deployed behind perimeter security measures on the servers and workstations that compose the network.
Tripwire software works in a number of ways to ensure the integrity of your network. Because of its ability to detect intrusions, it is often deployed to “guard the guards”– to monitor the integrity of firewalls and network security appliances that are often themselves the target of attacks. At the same time, Tripwire software monitors all of the systems inside the firewall, detecting and reporting unexpected changes whether they come through the firewall or originate within the system.
…….
Course Unix installing and running the Tripwire product (3614 KO) (Cours PDF)