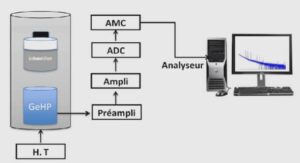
- Saturday
- April 27th, 2024
- Ajouter un cours
Cours How to Build a Perfect Database Every Time, tutoriel & guide de travaux pratiques en pdf. How to Build a Perfect Database Every Time Building a good database is not rocket science. It is, however, computer science. If you...
Cours real-time multimedia composition using Lua, tutoriel & guide de travaux pratiques en pdf. ABSTRACT In this paper, a new interface for programming multimedia compositions in Max/MSP/Jitter using the Lua scripting language is presented. Lua is extensible and efficient making...
Cours Microsoft Excel 2010, tutoriel et guide complet Excel pdf. Workshop Information Learning Outcomes Format Additional Resources Help Feedback 3D Referencing Create a 3D Reference Exercise Data Tables – One Input tables Named Ranges Creating named ranges using the name...
Extrait du course and tutorial using Java with MySQL Architectures The client side may consist of only HTML and a web browser—athin client—or may contain compiled Java code in client-side web application modules. Server-side components may reside on any number of...
Working with Services Determining When to Use Services A service within the Android Software Development Kit (SDK) can mean one of two things. First, a service can mean a background process, performing some useful operation at regular intervals. Second, a...
Adding a Login Page Security under ASP.NET is a fairly large topic, and it's certainly not my intention to cover it here. However, in order to add security pages to the application, we must understand that security works at the...

Selling your application android Choosing the Right Distribution Model The application distribution methods you choose to employ depend on your goals and target users. Some questions you should ask yourself are n Is your application ready for prime time or...

MPLS VPN Technologies Chapter 2 provided some brief discussion of Virtual Private Network (VPN) architecture with respect to connectivity options for teleworkers. Remote-access VPNs and IPsec VPNs were both discussed along with some key differences between the two. Among the...
Analytics Business Maturity Model As I stated earlier, Big Data Analytics is a journey and can be implemented using a number of iterative phases, each advancing the capability via well-defined yet small steps to reduce risk. The Information Agenda team...