- Saturday
- May 18th, 2024
- Ajouter un cours
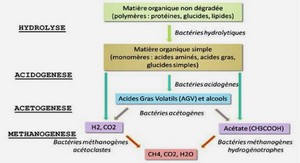
Cours programming Wireless Sensor Networks, tutoriel & guide de travaux pratiques en pdf. REFERENCE ARCHITECTURE The boundaries between programming abstractions and the rest of the software ex-ecuting on a WSN node is often blurred. The scarce computing and communication resources...
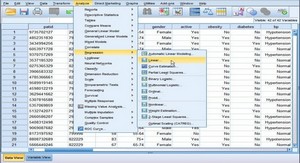
Cours Descriptive Statistics - involving one variable, tutoriel & guide de travaux pratiques en pdf. Descriptive Statistics - involving one variable The first step at the beginning of analysis is to run descriptive statistics (e.g. counts, averages, maximum, minimum, and...

Télécharger course wireless application group user agent profile specification, tutoriel free course PDF. 1 CONTENTS 2 REFERENCES 3 DEFINITIONS, ABBREVIATIONS, AND CONVENTIONS 3.1DEFINITIONS 3.2ABBREVIATIONS 4 INTRODUCTION 4.1SCOPE 4.2AREAS FOR FURTHER WORK 4.3RELATIONSHIP TO OTHER STANDARDS 5 END-TO-END ARCHITECTURE 5.1CLIENT DEVICE...
1. SCOPE 2. DOCUMENT STATUS 2.1 COPYRIGHT NOTICE 2.2 ERRATA 2.3 COMMENTS 3. REFERENCES 3.1 NORMATIVE REFERENCES 3.2 INFORMATIVE REFERENCES 4. DEFINITIONS AND ABBREVIATIONS 4.1 DEFINITIONS 4.2 ABBREVIATIONS 5. ARCHITECTURAL OVERVIEW 6. WAP SECURITY OPERATIONS 6.1 WTLS OPERATIONS 6.2 WAP...
Sommaire: Thinking in Java Overview What’s Inside... Preface 1: Introduction to objects 2: Everything is an object 3: Controlling program flow 4: Initialization & cleanup 5: Hiding the implementation 6: Reusing classes 7: Polymorphism 8: Holding your objects 9: Error...
Extrait du course developing the teaching of listening comprehension in english ....... B-WHILE LISTENING ACTIVITIES While-listening activities relate directly to the text, and students do them during or immediately after the time they are listening. If students are to complete a ...

........ Characteristics of a Defense in Depth Strategy A robust defense-in-depth strategy includes: A security risk management framework Identity and access management policies Network protection Update management Education Incident response Continual reassessment and optimization Layers in a Defense-in-Depth Strategy Policies...